It is difficult to navigate the constantly evolving world of compliance and regulations. Manual risk management often leads to gaps in security and requires high effort and collaboration to achieve compliance. Reaching compliance is a huge undertaking, often involving guesswork and extensive research just to have information to get started. By leveraging AWS Audit Manager and the VR Cloud Controls Framework, we can create a custom audit framework that meets our individual business requirements, automate the audit process, and attain routine compliance.
There are many industry-standard regulations for compliance. For example PCI, HIPAA, and GDPR. Figuring out the requirements to maintain in compliance with these standards as well as adhering to local laws and regulations where your data is processed is a strenuous task. An organization that is not compliant faces significant penalties and affects its business.
In this blog post, we will leverage AWS Audit Manager to check our initial state of compliance.
Then we will use the VR Cloud Controls Framework to efficiently find Cloud Control Matrix compliance requirements that our business must adhere to. Once we figure out the base requirements, the VR Cloud Controls Framework will also help us understand the functional requirements associated with each control, as well as a technical implementation to ensure our AWS services are in compliance.
Here are some key pain points financial services institutions face that we will address.
| Problem | Details |
| Assessing Initial Compliance State | The process for auditing existing infrastructure is time-consuming and costly. Many businesses do not know their current state of compliance. Standards change over time and it is difficult to keep up with new rules. |
| Finding Compliance Requirements | Finding the controls that are applicable to your business in the cloud control matrix. |
| Functional Requirements | The control specifications are often vague. It is hard to figure out what the exact “ask” is in our cloud infrastructure. |
| Technical Implementation | Understanding how the functional requirements map to different AWS services, and the changes we need to implement to our infrastructure. |
| Evidence of compliance | It is not enough to show that there are no security risks in your infrastructure. Concrete evidence of meeting compliance requirements must be provided. |
| Creating Compliance Reports | The process of creating compliance reports, whether, through CloudWatch, CloudTrail logs, or other data sources requires a lot of manual labor. Creating a report turns into a giant ETL job that is not replicable for future audits. |
| Automating Compliance Checks | Similar to creating compliance reports, the audit process as a whole requires a lot of manual intervention and labor. Piecing together information from third-party auditing tools is difficult to automate. |
AWS Audit Manager
The era of manual auditing processes is soon to be over. No more auditing fire drills, endless research, and countless hours to reach compliance. AWS Audit Manager is a new service that strives to make auditing simple. Let’s take a look at some of the key features of Audit Manager:
- Pre-Built Frameworks: AWS Audit Manager comes with pre-built frameworks that help map your resources to common industry standard control requirements such as PCI, HIPAA, and more. You can also customize these frameworks to your own specifications.
- Customize Assessment Scope: Once your framework is ready, you can choose which services and accounts fall under the assessment. This makes collecting evidence across accounts in your organization a lot easier.
- Automated Evidence Collection: With the vast number of services AWS offers, collecting evidence from each service to prove that you are in compliance is time consuming. AWS Audit manager collects evidence from your resources specified in the assessment scope at automated time intervals.
- Report Generation: Using the evidence collected, AWS Audit Manager automatically creates an assessment report. This report is organized by controls with the collected evidence. The report is presented in an audit-friendly format.
CSA Cloud Controls Matrix
The Cloud Security Alliance Cloud Controls Matrix (CSA CCM) is a framework that provides an approach on how to implement compliance in the cloud. The matrix contains controls that cover all aspects of cloud infrastructure. It is a valuable tool that is continuously evolving to meet the security demands of new technologies.
One of the key features of the CCM that we will utilize is control mapping. The controls in the CCM are mapped to industry-standard regulations such as PCI DSS, NIST, and CIS. Rather than going through each of these regulations’ requirements documents and trying to piece together what you need to implement, the CCM provides exactly what CCM control maps to the regulation control.
Solution
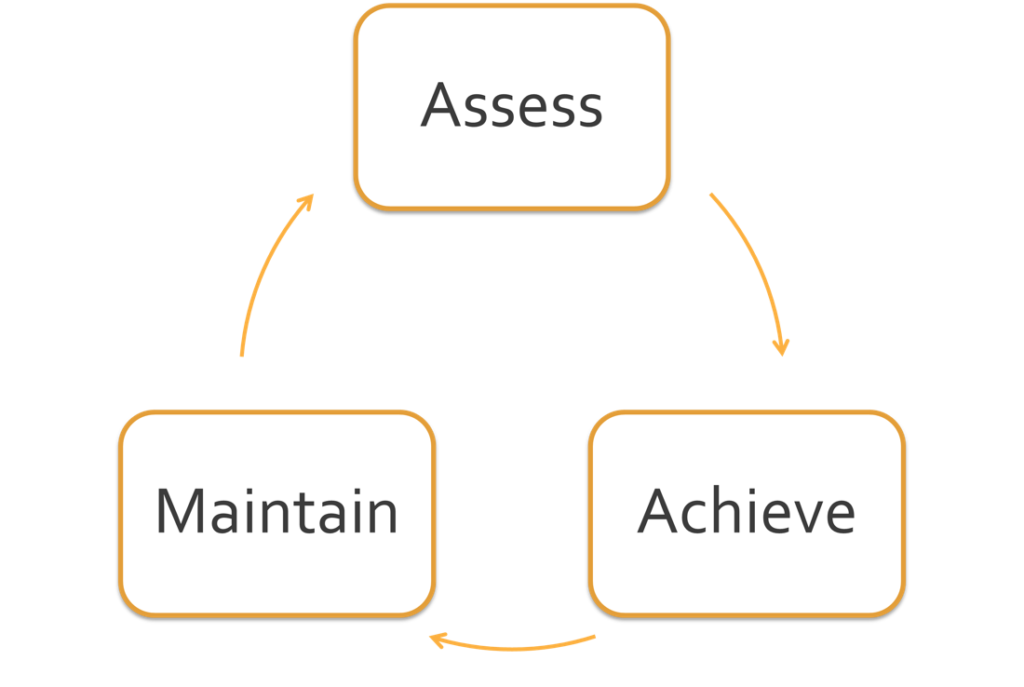
Our solution is broken into three main components: Assessing Initial Compliance, Achieving Compliance and Maintaining Compliance. The solution is quite a circular process. Once we achieve compliance our next step will be to assess once again. From this solution, we get a continuous motion of compliance.
Assessing Initial Compliance
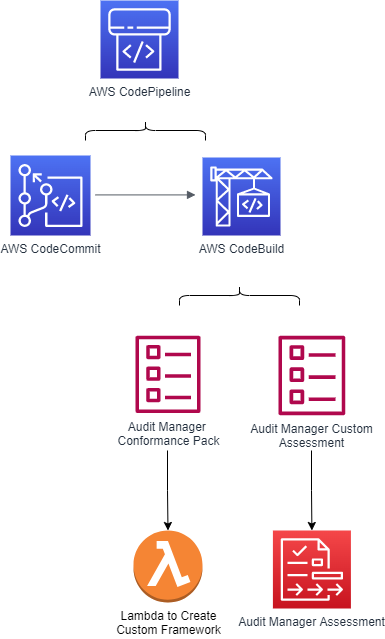
For our existing infrastructure, we need to assess the current level of compliance we have. Since compliance rules change over time, resources that may have been previously compliant could no longer be compliant. We will take an automated pipeline approach developed by Senior Cloud Consultant, Greg Hoggard for this problem.
The pipeline has two stages: source and build. First, the pipeline will pull our code from CodeCommit. The code consists of a mapping document that maps AWS config rules to compliance requirements. It also consists of a Lambda function that will create a custom Audit Manager framework based on the mapping document. Then, a custom assessment is created in Audit Manager. Once the assessment has run, it continuously collects data and presents it in the audit-ready report. The report will show our current level of compliance.
Achieving Compliance
In order to reach compliance, we need to know what we are trying to be compliant with and how we are going to accomplish it.
- The What: The VR Cloud Controls Framework is a document developed by Associate Client Partner, Hunter Sneed that expands on controls from the Cloud Security Alliance Cloud Controls Matrix (CSA CCM). By working through this document, we can determine which controls are applicable to our business. Once we identify the necessary controls, from there the framework breaks down each control into functional requirements. Each functional requirement expands on the control specification in the Cloud Controls Matrix and clearly states what needs to be implemented in our cloud infrastructure.
- The How: Every functional requirement has one or more technical requirements. The technical requirements describe what adjustments need to be made to your AWS Services in order to achieve compliance. Every technical requirement also has code samples in both CloudFormation and Terraform so you can easily implement these changes in your infrastructure.
Features and information provided in the VR Cloud Controls Framework will be further expanded upon during the implementation phase of this blog.
Maintaining Compliance
Once we implement the steps to achieve compliance, we need to validate our work. The process is similar to assessing our initial state of compliance. When we validate our compliance we should see previous compliance issues resolved as a result of our efforts. The security standards we implemented will help us maintain compliance with future resources created.
Here are the proposed solutions to our problems, and the services we will use to solve them.
| Problem | Solution | Tools & Services |
| Assessing Initial Compliance State | Utilize AWS Audit Manager and create a custom framework of what we need to be compliant with. Then run an assessment from that framework to check our current level of compliance. | AWS Audit Manager |
| Automating Compliance Checks | Create a CodePipeline that sources a mapping document in CodeCommit to build an Audit Manager framework. Create and run a custom assessment in Audit Manager. | AWS CodeCommit, AWS CodeBuild, AWS CodePipeline, AWS Audit Manager, AWS Lambda, AWS CloudFormation |
| Finding Compliance Requirements | In the VR Cloud Controls Framework, each control ID from the cloud controls matrix is marked on applicability. For the financial services industry, we can see that relevant controls are marked as “applicable” and “potentially applicable”. | VR Cloud Controls Framework, Cloud Controls Matrix |
| Functional Requirements | The Functional Requirements section of the VR Cloud Controls Framework expands on what the cloud controls matrix is asking us to do. It is broken into key points to cover all ground. | VR Cloud Controls Framework |
| Technical Implementation | Each functional requirement has one or more technical requirements. The technical requirements clearly state what adjustments need to be made to which AWS Services. It includes information on how difficult the implementation is, along with a code sample on how to do it. | VR Cloud Controls Framework, CloudFormation/Terraform |
| Evidence of compliance | AWS Audit Manager automatically collects evidence of compliance for you across your AWS accounts and services. | AWS Audit Manager |
| Creating Compliance Reports | AWS Audit Manager automatically creates reports based on your selected criteria. The report is organized and presented in an easy to read auditor-friendly format. | AWS Audit Manager |
Implementation/Demo
Let’s walk through an example of our solution.
Assessing Initial Compliance: Code Repo Structure
Repository Structure
- Cfn Folder
- codepipeline.yaml – This file is a CloudFormation template that creates a codebuild project, the codepipeline, and necessary IAM roles
- aws-auditmanager-confpack.yml – This file is a CloudFormation template that creates a lambda function along with necessary IAM roles. The lambda function creates a custom framework in Audit Manager.
- aws-auditmanager-customassessment.yml – This file is a CloudFormation template that creates an Audit Manager Assessment using the custom framework created by the lambda function
- Buildspec.yaml – The build file for the codebuild project
- Lambda Folder
- CustomAuditManagerFramework_Lambda.py – This is the lambda function that creates a custom framework in Audit Manager
- Auditmanagerlayer – utilities for python and boto3
- Mapping File Folder
- Mappingcsv1.csv – This is a mapping file that maps NIST control IDs to AWS config rules
Deploy and Run the Pipeline
Download the repository and deploy the codepipeline.yaml CloudFormation template with the following command:
aws cloudformation deploy --template-file cfn/codepipeline.yml --capabilities CAPABILITY_NAMED_IAM --stack-name audit-manager-pipeline
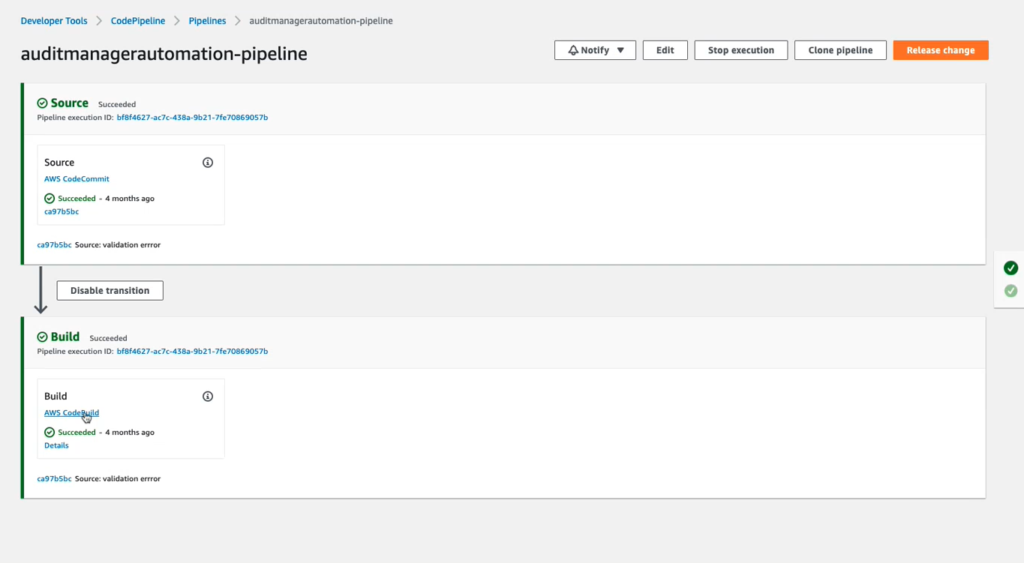
Great! Let’s check the status of the deployment in the console.
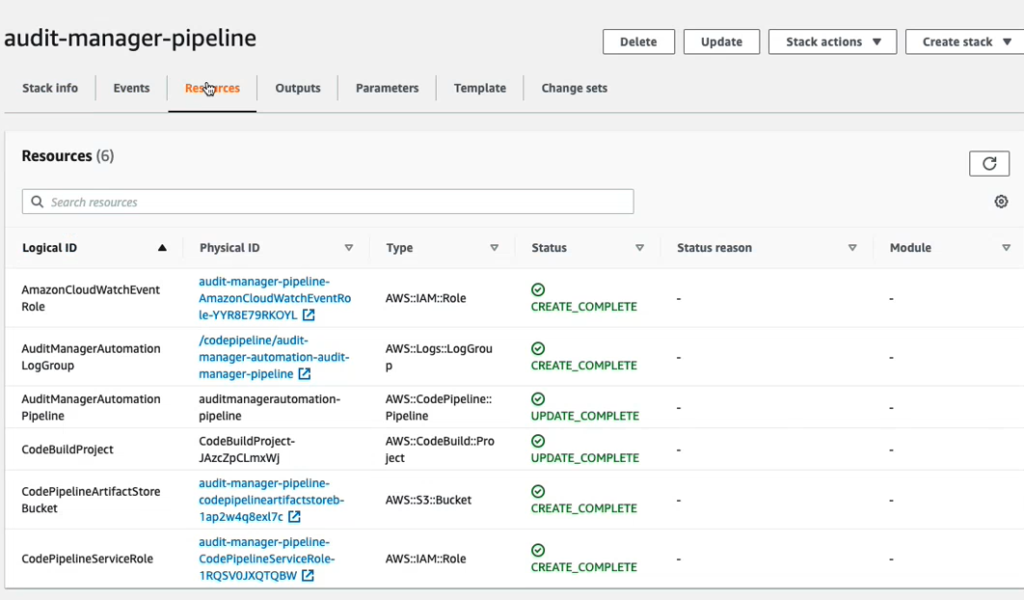
The pipeline has two stages, source and build.
Source Stage
- Code is sourced from repository
Build Stage
- AuditManagerLayer file is uploaded to S3 bucket
- Custom Audit Manager Framework Lamda is uploaded to S3 bucket
- Mapping file is uploaded to S3 bucket
- CloudFormation template aws-auditmanager-confpack.yml is deployed
- CloudFormation template aws-auditmanager-customassessment.yml is deployed
Navigate to CodePipeline in the console and run the pipeline.
Check the Assessment Report
In the console, go to Audit Manager and go to Assessment Reports. The report will show our compliance with the specified NIST controls in the mapping document.
Finding Compliance Requirements
After we assess our current state of compliance, our next step is to work through the VR Cloud Controls Framework. On page 01 of the spreadsheet, we see the standard Cloud Controls Matrix. There are several added features to this matrix. Here is the breakdown of the added features:
| Column Letter | Name | Explanation |
| B | Applicability | Use this column to mark whether or not the control is applicable to your business |
| F | Functional Requirements | This further explains the control specifications (column E) by breaking it down into requirements. |
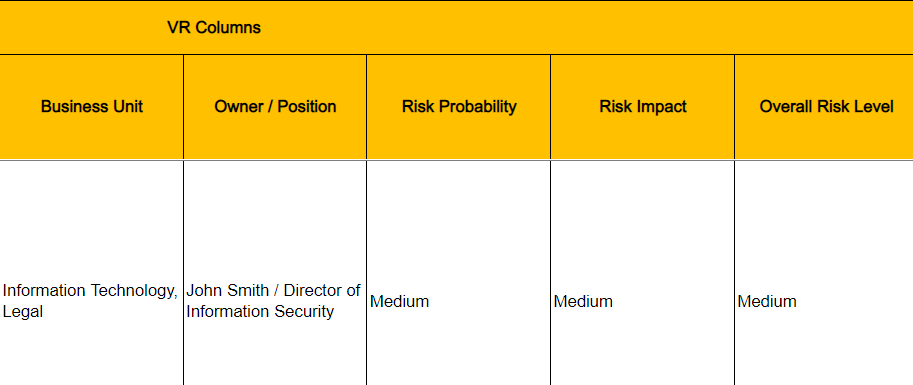
| G | Business Unit | The department the control relates to. |
| H | Owner/Position | Who is responsible for implementing this control within your organization |
| I | Risk Probability | The likelihood of a security event occurring if the control is not implemented. |
| J | Risk Impact | If the control is not implemented, and there is a security breach, this is the likely level of impact to expect. |
| K | Overall Risk Level | Overall risk level of not implementing the control. |
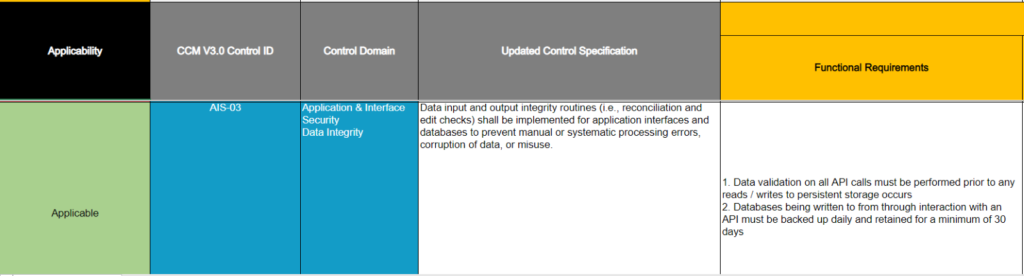
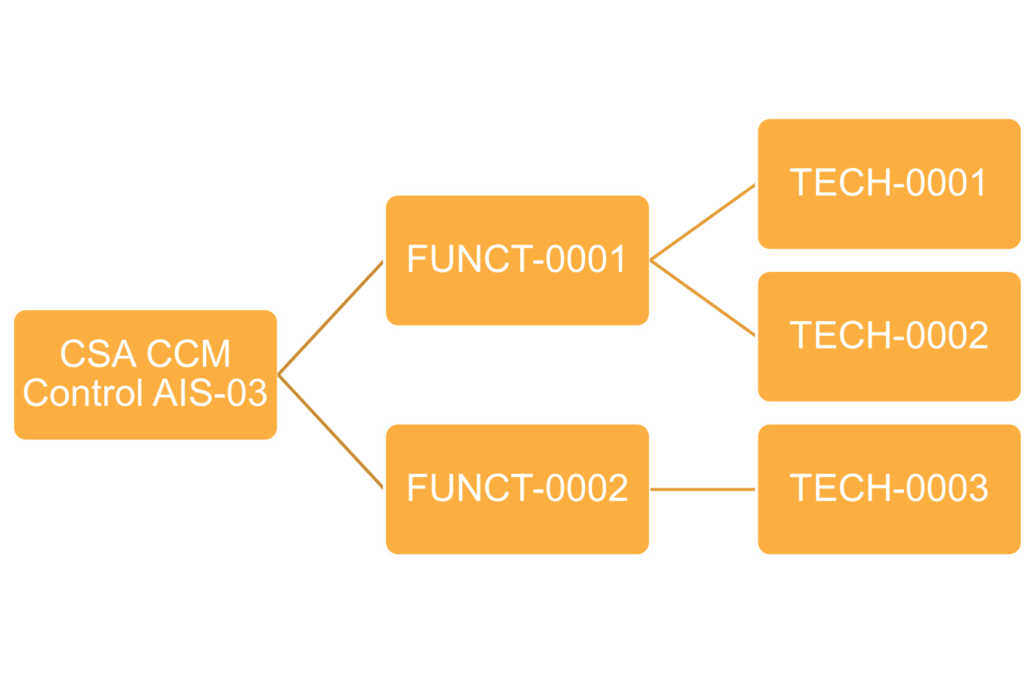
Our first step is to go through the entire document and mark which controls are applicable in column B. For the purposes of this demonstration, we will show how to implement one control, AIS-03 (row 14).
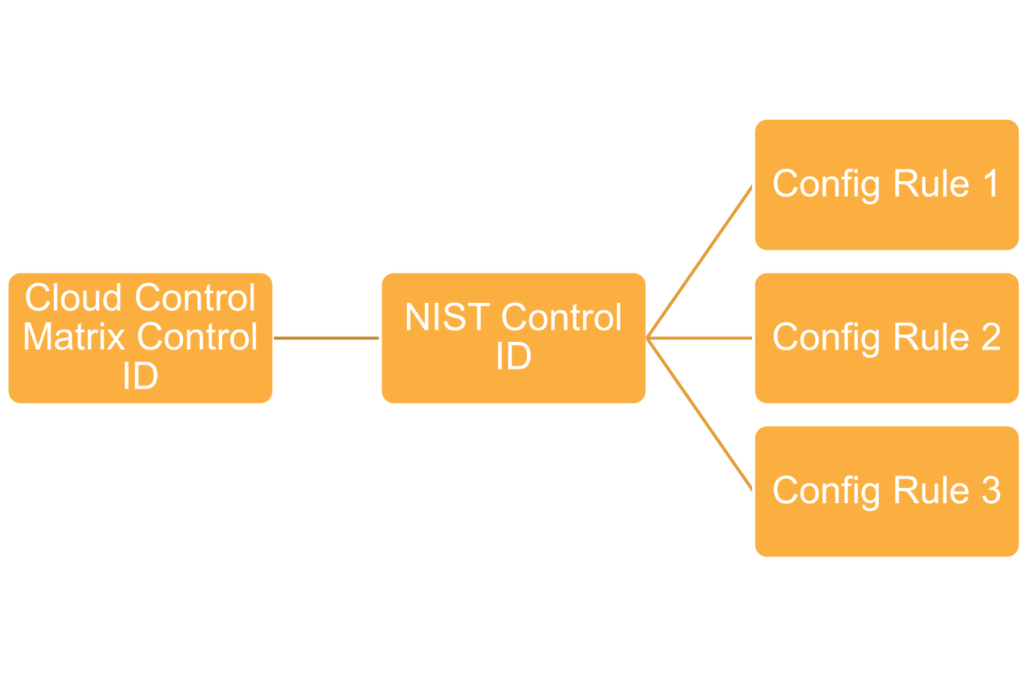
(Note that every control ID is also mapped to NIST control IDs under Scope Applicability, this will be relevant later)
Assessing Functional Requirements
We have marked that control AIS-03 is applicable to our business. Now we need to understand what the function of the control is.
Read the functional requirements for the control (column F). It contains two requirements that we need to implement.
Let’s move on to the next sheet 2 of the document. Here we get a further breakdown of each functional requirement specified in sheet 1. Here an explanation of each column on this page:
| Column Letter | Name | Explanation |
| B | Functional Requirement ID | The ID of the functional requirement. |
| C | Functional Requirement | Description of the functional requirement. |
| D | CSA-CCM Mapping | The control ID on page 01 that the functional requirement maps to |
| E | Control Domain | Relevant domain for the control |
| F | Risk Level | Risk imposed in the event that the functional requirement is not addressed |
| G | Remediation Effort | Estimated amount of effort needed to implement this requirement. |
| H,I,J | Control Audience | Audience for the control (people, process, or technology) |
| K,L,M | Control Type | Specifies whether the functional requirement is a preventative measure, detective measure, or responsive measure. |
| N – end | AWS Services | AWS Services that we will be working on when we do the technical implementation |
Read through the information provided for FUNCT-0001 and FUNCT-0002. This page will give you a heads up on what to expect before we go into the actual technical implementation. We see that for FUNCT-0001 we will be working with API Gateway. For FUNCT-002 we will be working with Amazon RDS.
Implementing Technical Requirements
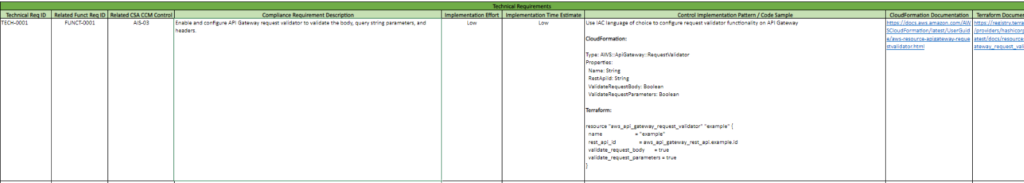
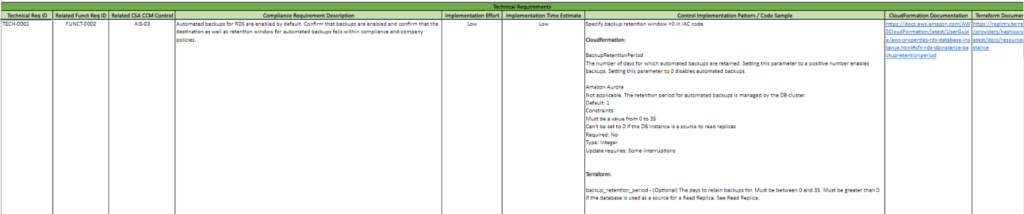
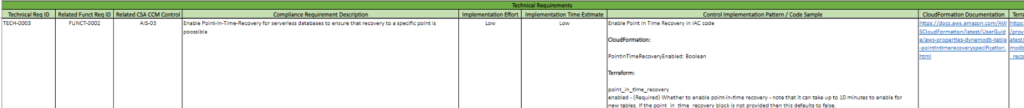
Now that we understand the two functional requirements necessary for the AIS-03 control, we can implement it into our infrastructure. Let’s take a look at page 03 – Technical Requirements of the VR Cloud Controls Framework. We see there are 3 technical requirements we need to implement. Here is an explanation of each column on this page:
| Column Letter | Name | Explanation |
| B | Technical Requirement ID | The ID of the technical requirement. |
| C | Related Functional Requirement ID | ID of the functional requirement that the technical requirement maps to. Note that there can be multiple technical requirements for one functional requirement. |
| D | Related CSA-CCM Control | The control ID on page 01 that the technical requirement maps to |
| E | Compliance Requirement Description | Explains exactly what changes will be made to our infrastructure and AWS Service |
| F | Implementation Effort | Estimated effort to implement the technical requirement (possible values: low, medium, and high) |
| G | Implementation Time | Estimated time to implement the technical requirement (possible values: low, medium, and high) |
| H | Control Implementation Pattern/Code Sample | The code sample shows you how to implement the technical requirement as infrastructure as code (IaC). Code sample is provided in both CloudFormation and Terraform. |
| I | CloudFormation Documentation | Link to the CloudFormation documentation |
| J | Terraform Documentation | Link to the Terraform documentation |
Implement the technical requirement into your infrastructure as code with the templates provided in column H. You can refer to the documentation links provided for further information about the code samples. Once we do this for all three technical requirements, we are in compliance with control AIS-03.
Maintaining Compliance
Let’s revisit the cloud controls matrix. Every control ID is mapped to NIST control IDs. Recall our mappings file, this file maps NIST control IDs to AWS Config Rules. We can simply add NIST control IDs to our document and find the associated config rules using this guide by AWS. Once we add that information and commit changes, our CodePipeline will run again and create a new assessment. Since we have implemented changes to our infrastructure using the VR Cloud Controls Framework, we should see that we are now in compliance
Conclusion
We have shown you how to automate the audit process by leveraging AWS Audit Manager and the VR Cloud Controls Framework. Our solution allows financial services institutions to save time, effort, and money in comparison to standard auditing procedures and provides a more secure cloud environment. If you are interested in using this solution for your business, contact us today