Overview
In today’s digital landscape, enterprises face the formidable challenge of managing security alerts across a myriad of platforms. The proliferation of detection tools such as Prisma, Trusted Advisor, and Carbon Black has underscored the urgent need for a consolidated approach to security alert detection and mitigation. The primary business problem lies in the fragmentation of security alert management, which complicates the process of timely and effective threat response, thereby increasing the risk of data breaches and cyber attacks.
Traditionally, businesses have tackled this issue by deploying multiple, vendor-specific tools to handle alert detection and mitigation. This approach not only leads to vendor lock-in but also escalates change management costs, hindering an organization’s ability to adapt to new threats swiftly. The reliance on a patchwork of solutions complicates the security landscape, making it difficult to scale responses efficiently across the enterprise.
In this playbook, we advocate for a fundamentally different approach to addressing the challenges outlined above. We propose a singularly unified and scalable solution designed to centralize control and facilitate cross-account remediation of security issues. By introducing an architecture that serves as a universal conduit for alert remediation, our solution enables a seamless integration with various detection tools. This approach pivots from the traditional method by focusing solely on the automatic remediation of identified security threats, rather than their detection.
There are numerous benefits of this proposed solution. By eliminating vendor lock-in, organizations gain the flexibility to choose and change their detection tools without incurring prohibitive costs or undergoing extensive system overhauls. Furthermore, our scalable architecture ensures that as an enterprise grows, its ability to respond to security alerts does not lag behind. This streamlines the management of security alerts and significantly reduces the time to remediation, enhancing the overall security posture of the organization. In this playbook, we delve into the specifics of implementing our unified solution, demonstrating how it outperforms traditional methods in efficiency, scalability, and adaptability.
Prescriptive Guidance
Before diving into Control Agent, it’s crucial to recognize its role in a complex cybersecurity ecosystem that transcends traditional boundaries, enabling an advanced posture of automated remediation processes. Far from being confined to AWS services, Control Agent stands out for its capacity to incorporate alerts from a wide range of sources, including third-party tools, other accounts, and various cloud providers, ensuring a truly unified security management framework. This adaptability underscores the solution’s commitment to providing a scalable, agile, and comprehensive approach to security threats, emphasizing seamless integration across platforms, scalability to handle evolving threats, and real-time visibility into security operations. As we explore Control Agent’s functionalities and deployment strategies, the emphasis will be on leveraging its extensive compatibility to enhance the security resilience of your cloud environment.
Definitions
- Active Controls – Security mechanisms implemented to directly prevent, detect, and mitigate unauthorized access or cyber attacks in real time. Examples include firewalls, intrusion prevention systems, and automated patching mechanisms. These controls are proactive in nature, ensuring immediate response to potential security threats.
- Detective Controls – Measures designed specifically for the identification and documentation of unauthorized activities within a system. They play a crucial role in alerting organizations to security breaches and are essential for incident response and forensic investigations. Log monitoring, intrusion detection systems, and access and security event auditing are common examples of detective controls.
- Custom Controls – Tailor-made security measures developed to address unique organizational requirements or specific risk scenarios not covered by standard controls. These controls can vary widely, from bespoke monitoring scripts to custom access management protocols, offering a high degree of flexibility in bespoke security risk management.
- Centralized Control Agent – A system or platform that consolidates management and oversight of security policies, procedures, and measures across an organization’s entire IT infrastructure. It facilitates centralized configuration, management, and enforcement of security protocols, streamlining administration tasks and ensuring a uniform security stance across varied environments.
- Source – Any origin point of security alerts or findings within the Control Agent ecosystem, including but not limited to, cloud services, internal security tools, and third-party security solutions. This definition encompasses the wide array of potential inputs into the Control Agent system for security event detection and response.
- Orchestration – The automated configuration, coordination, and management of computer systems, applications, and services. In the context of Control Agent, orchestration refers to the automated processes that manage the sequence of actions taken in response to security alerts, ensuring efficient and timely remediation.
- Remediation – The process of resolving security vulnerabilities or threats once they have been detected. Remediation actions can include applying patches, changing configurations, or removing compromised resources to mitigate potential damage and restore security.
Best Practices / Design Principles
In the pursuit of robust security operations, Vertical Relevance underscores the importance of a strategic framework when integrating Control Agent. We recommend starting with the establishment of a unified detection and remediation framework that seamlessly incorporates both AWS and third-party security tools. This should be complemented by streamlined orchestration processes, utilizing Control Agent’s automation capabilities to ensure rapid and efficient threat mitigation. By optimizing these workflows and leveraging data-driven insights from AWS OpenSearch and Managed Grafana dashboards, organizations can continuously refine their security strategies for heightened responsiveness and effectiveness.
Moreover, fostering a culture that prioritizes security awareness and adaptability is crucial. Regular reviews and updates of security policies and Control Agent configurations are advised to keep pace with the dynamic nature of cyber threats. This approach enhances the security posture and embeds a proactive security mindset within the organization, ensuring that teams are well-prepared to leverage Control Agent’s full potential in safeguarding their cloud environments.
Through these consolidated practices, Vertical Relevance aims to guide organizations in harnessing Control Agent’s capabilities to create a more secure, agile, and resilient IT infrastructure.
Detection
Components
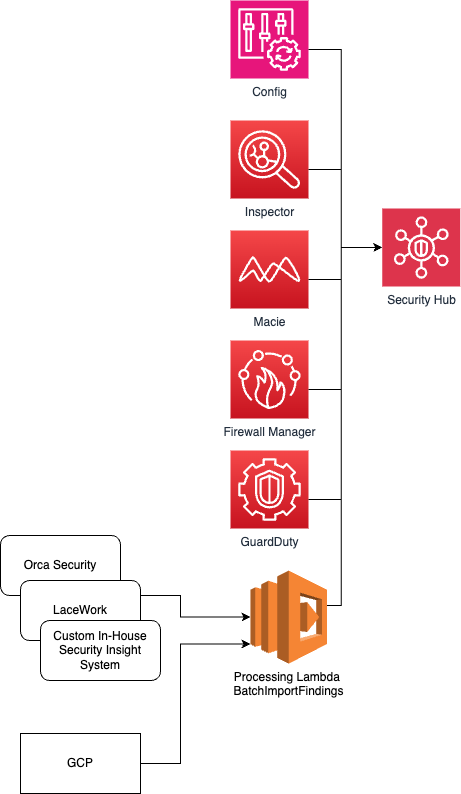
- AWS Config – Security Hub can receive input from AWS Config rules to alert on resource configurations to keep them automatically aligned to best practices using Control Agent based automated remediation
- AWS Inspector – All findings are aggregated in Amazon Inspector, then routed to AWS Security Hub to automate remediation with Control Agent
- AWS Macie – A data security service that discovers sensitive data by using machine learning and pattern matching. Integrating this with Security Hub and Control Agent enables automated remediation and protection against detected risks
- AWS Firewall Manager – Integration with Security Hub and Control Agent will allow for automated remediation of many types of findings
- AWS GuardDuty – Security Hub can integrate with AWS GuardDuty, which will facilitate Control Agent to automatically remediate security issues based on findings
- AWS Security Hub – Findings from all different security detection products, including 3rd party tools and allows for a central place to aggregate findings and coordinated automated remediation
- Other internal or third party products
How it works
Control Agent begins its security management process with a comprehensive detection phase. By integrating a variety of detection tools, the framework ensures wide coverage across different environments and threat vectors, enabling real-time identification of potential security issues.
Figure-01
- Detect: Security detection tool (Inspector, Macie, LaceWork, custom solution, etc) identifies issue and submits finding to Security Hub
Blueprint
This blueprint includes the Orchestrator pipeline to deploy the Orchestration layers and Member account layers using the CDK framework.
- Security Inputs – The pipeline is created through CDK, which will allow the user to easily deploy this pipeline to create the central Detection layer.
Automatic Remediation
Components
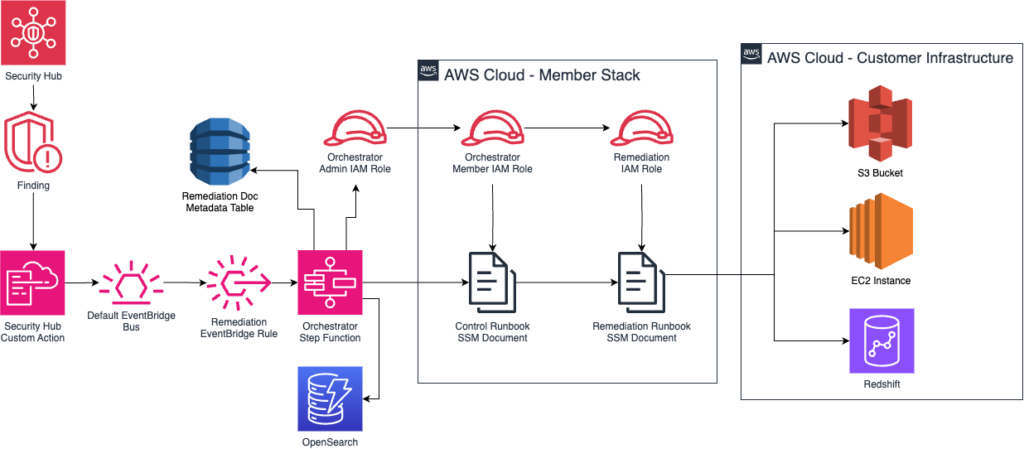
- AWS EventBridge – Security Hub findings are funneled into the EventBridge Rules to start the automated remediation process using the Step Function
- AWS Step Functions – Used to orchestrate the process of automated remediation for a given finding
- AWS SSM Runbooks – Used to perform the automated remediation and then report back the results
- AWS OpenSearch – Used to store the results of the automated remediation and document the findings
- AWS Managed Grafana – The data from the OpenSearch database displayed in a Grafana dashboard to show Control Agent status and remediation history
How it works
Upon detecting a threat, Control Agent swiftly moves to the heart of its functionality – automatic remediation. This phase leverages AWS services like AWS Step Functions and AWS SSM Runbooks to orchestrate and execute remediation actions without manual intervention, ensuring a rapid response to identified threats.
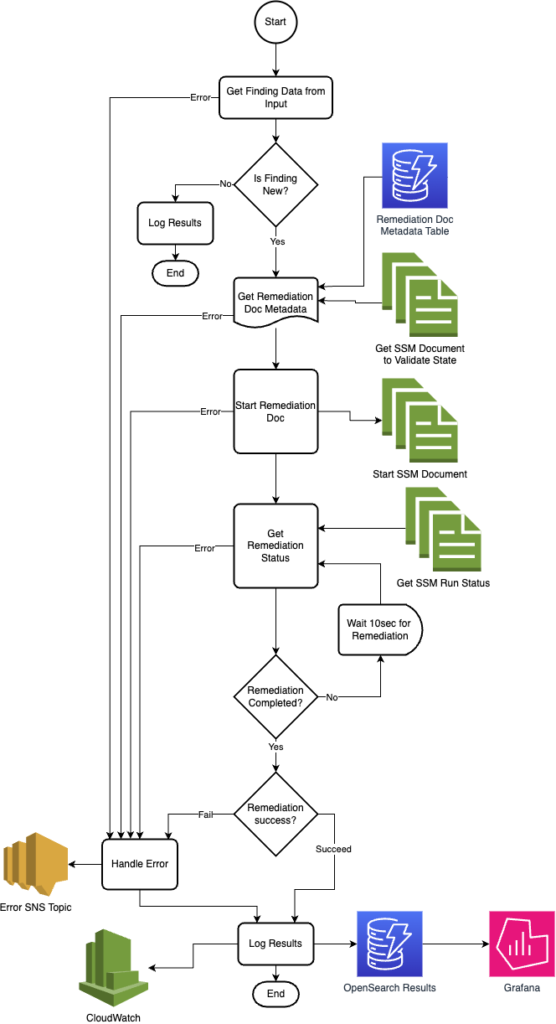
Figure-02
Figure-03
- Start Orchestration: Through an EventBridge rule, Security Hub starts the Orchestrator step function.
- Get Remediation Metadata: Based on the finding id, get the remediation metadata from the DynamoDB table and the SSM Runbook document.
- Start Runbook: Using SSM to start the Runbook in the Member Stack to remediate the security issue.
- Log Results: Store the log results in OpenSearch and CloudWatch.
Blueprint
This blueprint includes the Orchestrator pipeline to deploy the Orchestration layers and Member account layers using the CDK framework.
- Orchestrator CDK Pipeline – The pipeline is created through CDK, which will allow the user to easily deploy this pipeline to create the central Orchestration layer.
- Member CDK Pipeline – The pipeline is created through CDK, which will allow the user to easily deploy this pipeline in whichever Member account necessary.
Reporting
Components
- AWS OpenSearch – Used to store the results of the automated remediation and document the findings
- AWS Managed Grafana – The data from the OpenSearch database displayed in a Grafana dashboard to show Control Agent status and remediation history
How it works
The final pillar of Control Agent’s approach is its comprehensive reporting mechanism. This phase ensures that all actions, from detection to remediation, are logged and analyzed. It provides stakeholders with actionable insights into the security landscape and the effectiveness of the implemented measures.
Figure-04
- Display Dashboard: Display the results in a Grafana dashboard.
Blueprint
This blueprint comprises of the Orchestrator pipeline to deploy the Reporting layers and Member account layers using the CDK framework.
- Dashboard CDK – The dashboard is created through CDK, which will allow the user to easily deploy this dashboard to create the central Reporting layer.
Benefits
- Enhanced Security Posture: Rapid identification and automated remediation of threats strengthen the overall security framework.
- Centralized Security Management: Consolidates alerts for simplified oversight, improving efficiency and clarity in security operations.
- Scalability and Flexibility: Adapts to organizational growth and can integrate with a broad range of security tools, ensuring long-term viability.
- Cost Efficiency: Reduces the need for manual intervention, lowering operational costs associated with security management.
- Improved Incident Response Time: Accelerates the process from detection to resolution, minimizing potential damage from security threats.
End Result
Control Agent epitomizes the synergy of automation and integration for superior cloud security, encapsulating the journey from threat detection to remediation within a unified framework. By integrating detection tools, centralizing alerts via AWS Security Hub, orchestrating actions through AWS Step Functions, and executing remediation with AWS SSM Runbooks, it ensures a proactive defense mechanism. Coupled with real-time monitoring through AWS Managed Grafana, Control Agent enhances security responsiveness and solidifies organizational resilience against cyber threats, showcasing a groundbreaking approach to automated security management.