Infrastructure is one of the most fundamental requirements of an Organization. Teams often need a large variety of different infrastructure solutions and they often want to customize them to their particular use cases.
The Infrastructure Foundations solution enables development and operations teams to request different infrastructure products that come with all of the necessary components, integrations, and configurations. Each infrastructure product is tested and validated to comply with security and governance and is accessible through self-service.
Infrastructure Foundation Blueprint
Infrastructure Product
Infrastructure products provide development teams a ‘one-click’ mechanism to get a fully provisioned infrastructure solution. Infrastructure products take care of the setup, configuration, and installation of everything so the development team can simply utilize the product after requesting it.
An Infrastructure Product often only relies on the AWS Account, AWS Networking, and AWS Service Catalog deployment model to be in place.
Components
- CloudFormation – Infrastructure products are often defined using CloudFormation
- Service Catalog – Infrastructure CloudFormation templates are stored in Service Catalog as products where they can be launched by users or other Service Catalog products
- Ansible – For infrastructure that needs to be configured once it is launched, a configuration management solution is used
How it works
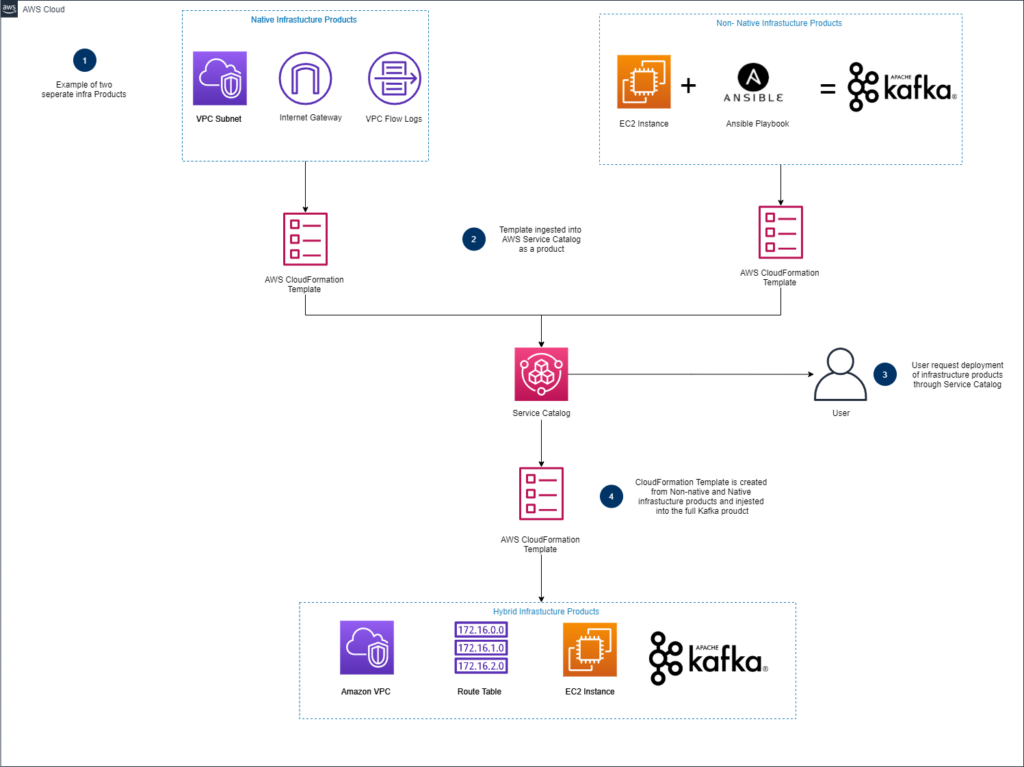
An organization will have various infrastructure products. These are often a variety of AWS Services and customized solutions combined to solve a particular infrastructure need:
- Native Infrastructure Products – These are infrastructure products that leverage and configure a set of AWS services to create an infrastructure solution.
- Customized Infrastructure Products – These are infrastructure products that are not native AWS services and require customized configuration management solutions to fully create an infrastructure solution.
Infrastructure products are then stored in AWS Service catalog where they can be consumed by development teams.
- Various Infrastructure products are defined in CloudFormation and are stored in version control
- VPC with Subnets, Route Tables, Internet Gateway, and VPC Flow Logs
- Customized Kafka Cluster
- Hashicorp Vault secret repository
- For native infrastructure products, the AWS Services are configured and connected
- For customized infrastructure products, once the underlying infrastructure resources are provisioned, a configuration management solution, such as Ansible, is used to properly configure those resources.
- The infrastructure products are stored in Service Catalog where it can be launched.
Storing the CloudFormation templates for Products in a source control repository like AWS CodeCommit allows the entire organization to understand how the Products are implemented. If the development teams need specific infrastructure for their solutions, they can develop entirely new CloudFormation templates and open Pull Requests with those changes, so that their new templates can be reviewed and approved.
Blueprint
Infrastructure Foundations Blueprint contains all of the CloudFormation templates and automation scripts needed for an end-to-end self-service CI/CD pipeline capable of delivering infrastructure-based Service Catalog Products to Service Catalog.
Infrastructure Factories
While Service Catalog provides a good way to share approved infrastructure configuration with the entirety of an organization, building a pipeline to approve and deliver those Products allows teams to innovate on their own, but still adhere to best practices and an organization’s own security controls.
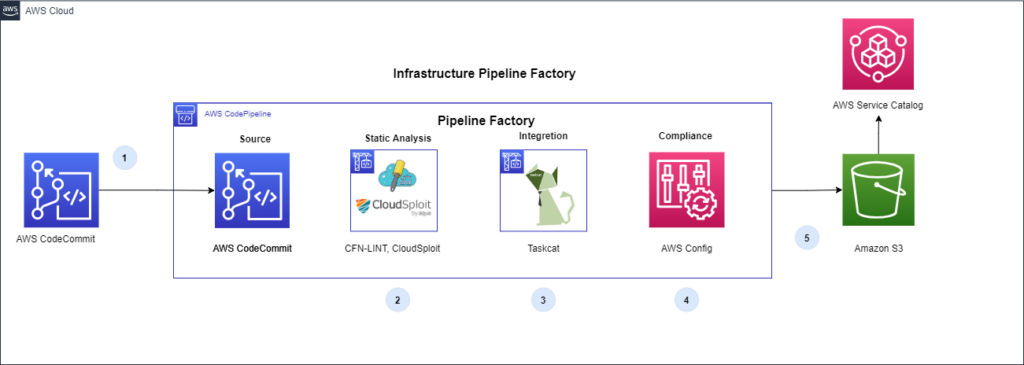
An automated pipeline takes care of running a series of automated checks against the CloudFormation template (such as running config_lint or taskcat), as well as other tests your organization requires. After all the checks pass, the pipeline automatically provisions the new Product inside Service Catalog and is ready for distribution
Components
- Cfn_Lint – For infrastructure static analysis
- Taskcat – For infrastructure integration testing
- AWS Config – For infrastructure compliance testing
How it works
When updates are pushed to a CloudFormation template in a git repository, a pipeline is automatically triggered to perform code linting and compliance testing against the new version of the template. The CloudFormation template is deployed into a new stack in an AWS account designated for testing. Once deployed, AWS Config compliance rules are evaluated to determine if the template complies with the organization’s cloud security and governance policies.
- Commit: Pulls the CloudFormation template from its version control repository
- Proactive Security Check:
- cfn_lint: Validate CloudFormation yaml/json templates against the CloudFormation spec and additional checks. Includes checking valid values for resource properties and best practices.
- cfn_nag: Static security analysis of CloudFormation templates. Checks template for insecure infrastructure such as:
- Overly permissive IAM and Security Group rules
- Password literals
- Encryption that is not enabled.
- Proactive Integration Testing: Taskcat deploys the AWS CloudFormation template in multiple AWS Regions and generates a report with a pass/fail grade for each region
- Reactive Security Check (Optional): The CloudFormation template is executed in an isolated AWS Account and AWS Config rules are used to check the built resources for compliance.
- Deployment to Service Catalog: The Service Catalog Product is deployed to Service Catalog, a Service Catalog Portfolio is created, the Product is added to the Portfolio, and access is granted to defined IAM users. Now the infrastructure product is ready for development teams to consume.
Blueprint
Blueprint/pipeline Contains a CloudFormation template for a CI/CD pipeline that will validate, test, and upload Infrastructure Service Catalog products into Service Catalog.
Benefits
- An organization has their “gold standard” for the particular infrastructure solution and it can be consumed at scale through self-service
- Infrastructure are codified to adhere to corporate standards and continually tested as changes occur through the infrastructure factories
End Result
The end result is a self-service method for development teams to request infrastructure. The infrastructure products are built through a deployment pipeline ensures that infrastructure can be developed upon while adhering to cloud best practices and your internal security controls.
Interested in learning more?
If you are looking to provide automation, consistency, predictability, and visibility to your software release process contact us today.